Breach Notification , Cybercrime , Cybercrime as-a-service
QNAP Tells Users to Take Immediate Action to Stop Ransomware
Ransomware Operators Targeting All Networking Devices
QNAP, a Taiwan-based company that manufactures network-attached storage devices, is urging users to take immediate action to secure its QNAP NAS device suite amid reports of wide targeting of all its networking devices by ransomware and brute-force attacks, the company stated in its security advisory.
See Also: Ransomware Response Essential: Fixing Initial Access Vector
The two types of ransomwares that are targeting QNAP NAS devices are Qlocker and eCh0raix, the company confirms to Information Security Media Group. "Qlocker, as the name suggests, targets the improper authorization vulnerability of QNAP devices, whereas eCh0raix is a new variant of ransomware that resorts to brute-force attacks on QNAP NAS devices, which also happens to be the most common form of cyberattack on NAS devices," a company spokesperson tells ISMG.
"Ransomware and brute-force attacks have been widely targeting all networking devices," says the company’s security advisory, which advises QNAP users to follow the security setting instructions prescribed by the company.
Even though all network storage devices are equally exposed in the ongoing campaign, according to the advisory, internet-facing NAS devices are more at risk, QNAP says. "The most vulnerable victims will be those devices exposed to the internet without any protection," the advisory says. To confirm whether your NAS device is exposed to the internet, QNAP suggests opening the "Security Counselor" setting on the QNAP NAS console.
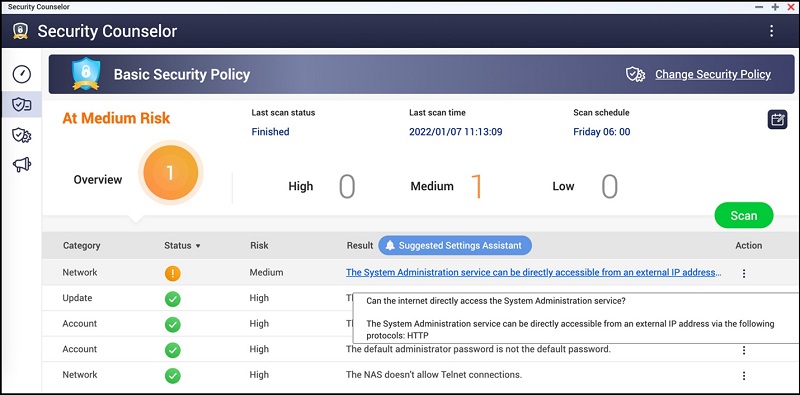
QNAP confirms whether your NAS device is exposed to the internet and thus at a very high risk of being targeted if the dashboard shows the following message: "The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP"
To confirm which exact ports are exposed to the internet unnecessarily and need to be taken offline, QNAP suggests users read this blog post.
Exposed? Do the Following
If the NAS device is found to be exposed in the Security Counselor console, QNAP recommends its users take the following two-step measure for securing their NAS devices:
- Disable the Port Forwarding function of the router: This can be done by navigating to the management interface of the router. Check the Virtual Server, NAT or Port Forwarding settings, and disable the port forwarding setting of NAS management service port [port 8080 and 433 by default].
- Disable the UPnP function of the QNAP NAS: Navigate to myQNAPcloud on the QTS menu, click the "Auto Router Configuration" and unselect "Enable UPnP Port forwarding."
Although this reconfiguration effectively pulls the NAS device offline, the company suggests some secure ways to access QNAP NAS via the internet through the myQNAPcloud link.
Apart from the mitigations prescribed, the QNAP spokesperson suggests implementing the following 3-2-1 backup rule.
- 3: Keep 3 copies of important files - 1 primary and 2 backups.
- 2: Keep the files on at least two types of storage media to protect against various hazards.
- 1: Store one copy off-site 0 outside your home or business.
The QNAP spokesperson tells ISMG that without the above security controls and protections in place, QNAP NAS devices should never be directly connected to the internet.
Major Outage
QNAP published the advisory last Friday, but some users over the weekend experienced their QNAP NAS devices crashing even when they were supposedly not exposed to the internet, as the security advisory suggested.
My QNAP NAS crashed last night and apparently I'm not the only one who has the exact same issue: https://t.co/GKWy4hVNr3
— OverSoft (@OverSoftNL) January 9, 2022
No ports exposed to the internet, not managed by the cloud.
QNAP is starting to look a lot like Ubiquiti: it starts off excellent and gets horrible over time
A tech blogger using the name Hardisk tweeted that there must have been zero-day flaws in the QNAP NAS devices. He says on Twitter that he used the antivirus/malware removal provided by QNAP, and the problem he found seems to be bigger than originally thought, as "no trace of the virus" was spotted in this malware detector.
The blogger says he had a cloud backup that prevented a complete data loss and used this backed-up data to restore operations.
Several users across the globe experienced similar QNAP NAS device outages, which they discussed on Reddit.
A user named Laaif says that he has more than 12 QNAP devices running, and 10 of them were not reachable on Sunday. A user named vdosen1963 says he faced a similar ordeal where two of his three NAS devices stopped working around the same time that others reported theirs to be dysfunctional, which was around 5:00 p.m. in the UTC+1 time zone. Data and snapshots was not affected, and an anti-malware scan found nothing, the user says.
Qlocker and eCh0raix Ransomware
The eCh0raix group was first seen targeting the QNAP storage devices in June 2019, when the operators exploited vulnerabilities in these devices and bypassed weak credentials using brute-force techniques. This seems to be the method used in the ongoing campaign (see: Report: Ransomware Targets QNAP Storage Devices).
In April 2021, the same group, along with another ransomware strain called Qlocker, again targeted QNAP devices - exploiting three known vulnerabilities at the time (see: QNAP Systems' Appliance Users Hit by Ransomware).
2022 seems to be heating up already, says Terry Greer-King, vice president, EMEA, at SonicWall. "While it's risky to make predictions on how cybercriminal activity will grow, the 2021 figures show us that ransomware is escalating at record pace," Greer-King tells ISMG. "We have witnessed a cyber surge in the year gone by. Overall, an unprecedented total of 714 million ransomware attacks were predicted by the close of 2021. It is highly unlikely that this will slow down in 2022."
Dmitriy Ayrapetov, vice president of platform architecture at SonicWall, says ransomware operators are mixing and matching malware ingredients deployed during the attack and escalating their techniques beyond phishing. Organizations need to protect their outward-facing attack surface, he says, and establish internal barriers, such as segmentation, to prevent the lateral exploitation that attackers rely to establish persistence and expand network access once they have established a foothold on a single system.





















