Fraud Management & Cybercrime , Fraud Risk Management , Next-Generation Technologies & Secure Development
New Hacking Group Exploits Vulnerabilities in Web Apps
Sygnia: 'Praying Mantis' Targets Checkbox Survey Flaws and Others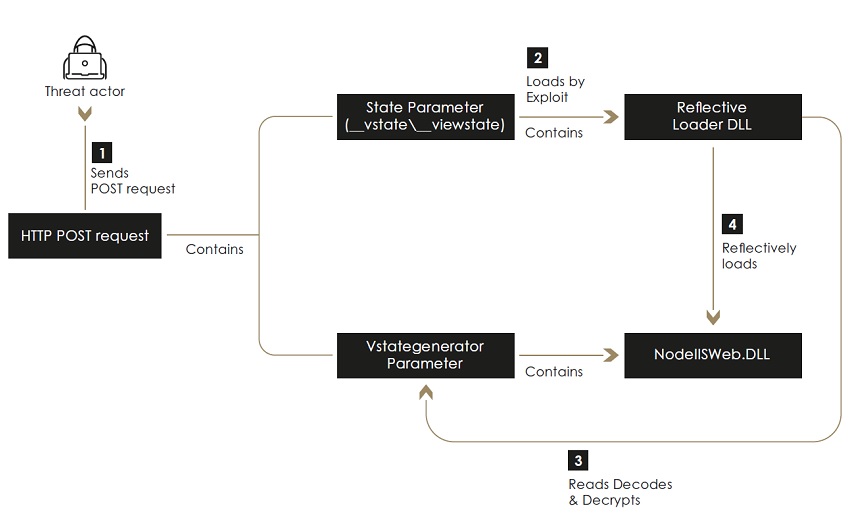
A newly discovered threat group dubbed Praying Mantis is targeting businesses in the U.S by exploiting vulnerabilities in internet-facing web applications to steal credentials and other data, the security firm Sygnia says.
See Also: New OnDemand | Cyber Risk Graph: Solving the Data Problem of Proactive Security
Sygnia, which also refers to the threat group as TG1021, says the campaign has been ongoing since June 2020. In some cases the group exploits a zero-day vulnerability in Checkbox Survey, a cloud-hosted survey and report analysis platform, which enables it to compromise Windows Internet Information Service servers used for web hosting.
After exploiting a flaw, the group deploys a malware backdoor to gather system information and deploy additional Java Script malware and perform HTTP and SQL traffic forwarding, Sygnia says in a new report. The additional payloads then harvest credentials and compromise more vulnerable servers.
"The threat actor uses an arsenal of web application exploits and is an expert in their execution," Sygnia says. "The swiftness and versatility of operation, combined with the sophistication of post-exploitation activities, suggest an advanced and highly skillful actor conducted the operations."
The campaign mainly targets companies in the U.S., says Arie Zilberstein, vice president of incident response at Sygnia. The security firm reported how Checkbox Survey insecurely deserializes ASP.NET View State data to the CERT Coordination Center, which issued an advisory on May 25.
Hacking Campaign
Sygnia notes the hackers exploit a remote code execution vulnerability in Checkbox Survey tracked as CVE-2021-27852. This vulnerability arises from the web application's viewstate mechanism in .net software framework in Windows, it adds.
"Viewstate is a mechanism in .net used to maintain and preserve web page session data between a client and a server. The vulnerability in Checkbox Survey was identified on a specific webpage in the application where the methods originally used to handle the viewstate mechanism were replaced with an insecure and compressed version called vstate," the report notes. "Sending a crafted vstate variable which exploits the 'LosFormatter' deserialization process would allow a threat actor to execute code remotely on the Checkbox application server.
Deserialization is a process that takes data from a file, stream or network and rebuilds it into an object. The report notes the hackers exploit the viewstate deserialization flaw to deploy a malware backdoor called NodeIISWeb. The malware then uses a DLL file to decode and decrypt encrypted data needed for compromising the IIS webservers.
The threat actors also leveraged another deserialization flaw in Checkbox Survey to deploy the Nodeshell backdoor, the report notes.
In attacks exploiting the Checkbox vulnerabilities, the malware performs tasks such as "IIS hooking," in which hackers analyze the incoming HTTP traffic, after which the operators send crafted HTTP requests to any webpage. The malware then performs tasks, such as gathering system information, and performs HTTP, SQL traffic forwarding and network tunneling, the report notes.
The malware backdoor then deploys second-stage malware, which then performs system information gathering. In the final stage of the attack, the hackers modify the victim's login webpages for credential harvesting.
"After establishing a foothold on an external IIS server, the threat actor accesses shared folders on internal web servers over SMB using compromised domain credentials. On several occasions, the threat actor dropped the NodeIISWeb web shell loader via SMB to compromise additional servers," the report notes.
Attribution
Sygnia notes the tactics and techniques used by the threat actors are similar to those of another campaign described by the Australian Cyber Security Center in June 2020. That campaign, dubbed Copy-Paste, targeted Australian government, political and educational organizations using public-facing servers.
Although the Australian government said the attack group it tracked was suspected to have links to China, Sygnia researchers note they did not have conclusive evidence to make an attribution of nation-state links to Praying Mantis.