Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management
More Zero-Day Exploits For Sale: Report
APT Groups Are Buying Exploits Rather Than Developing Them, FireEye Says
(This article has been updated)
See Also: The State of Organizations' Security Posture as of Q1 2018
Zero-day exploits are increasingly a commodity that advanced persistent threat groups can purchase and use to wage attacks, according to a report from security firm FireEye. The report says the number of attacks leveraging such exploits grew last year.
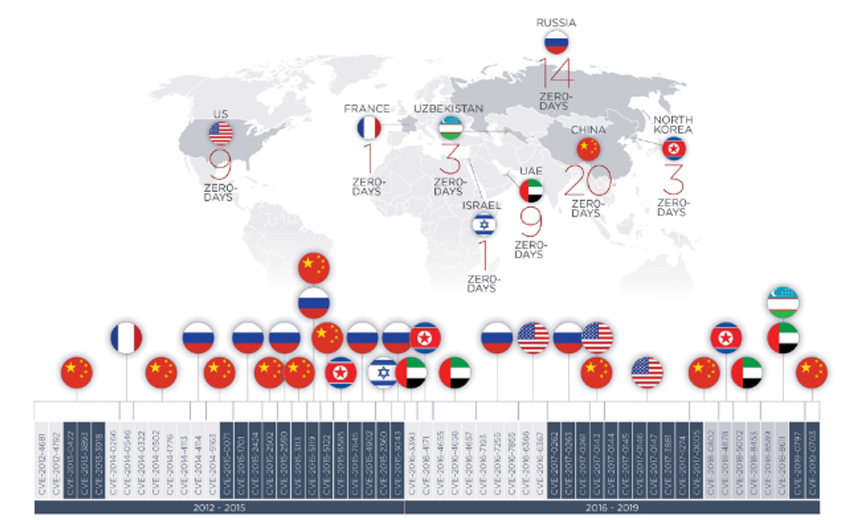
FireEye tracked the activities of APT groups and other malicious actors between 2016 and 2019 that leveraged zero-day vulnerabilities. Although the majority of these attacks were carried out by sophisticated APT groups, less technically adept groups also are increasingly using zero-day exploits that they’ve purchased as a commodity, the researchers say.
The Israeli firm NSO Group is among the companies that are offering exploits for sale, the report notes. Over the last year, the company has come under increasing scrutiny for selling offensive cyber capabilities that allegedly have been used to spy on journalists and activists (see: NY Times Reporter Targeted by Spyware: Report).
"Private companies are likely creating and supplying a larger proportion of zero-days than they have in the past, resulting in a concentration of zero-day capabilities among highly resourced groups," according to the FireEye research.
A spokesperson for the NSO Group denies that the company sells any zero-day exploits. "The company provides intelligence and analytic products, and not exploits. NSO's products are regulated and controlled, and are licensed only to governments for the purpose of countering terrorism and preventing serious crime," a company spokesperson tells Information Security Media Group.
Lowering the Cost of Attacks
The FireEye researchers point out that buying zero-day exploits can be far more cost-effective than trying to develop them from scratch.
"As a result, we expect that the number of adversaries demonstrating access to these kinds of vulnerabilities will almost certainly increase and will do so at a faster rate than the growth of their overall offensive cyber capabilities - provided they have the ability and will to spend the necessary funds," the report states.
APT Group Activities
The FireEye researchers say that an APT group called Stealth Falcon used malware designed by NSO Group to target journalists and activists in the Middle East during 2016.
Stealth Falcon, which is also referred to as FruityArmor, is believed to have ties with the United Arab Emirates and has been active since 2012, according to a report by Citizen Lab, a think tank based at University of Toronto.
Another APT group called SandCat, which researchers believe has ties to Uzbekistan state intelligence, has also purchased zero-day exploits from third-party providers, according to FireEye. Previously, Vice reported that this group purchased at least four zero-day exploits before security researchers discovered its operations.
The FireEye report also says that NSO Group exploited an Android zero-day vulnerability, dubbed CVE-2019-2215 in October 2019 to distribute spyware developed by the company.
In October 2019, Facebook announced that it had filed a lawsuit against NSO Group, claiming that the company developed this zero-day exploit to spy on WhatsApp messages from diplomats, journalists, human rights activists and political dissidents (see: Facebook Sues Spyware Maker Over WhatsApp Exploit).
Financial Pursuits
In addition to APTs with apparent ties to nation-states, the FireEye report finds that some other financially motivated attack groups are buying zero-day exploits as a commodity.
For example, the group known as FIN6, which has been linked to large-scale payment card thefts as well as ransomware attacks, appears to have purchased a zero-day exploit to use against certain versions of Windows Server as part of some of its attacks in 2018. The FireEye researchers believe this exploit was purchased from an underground hacker called "BuggiCorp," although no definitive link has been found.






















