Cloud Security , DDoS Protection , Incident & Breach Response
Microsoft Mitigates 'Largest Known DDoS Attack'
At Peak, the Throughput of the Attack Was Recorded as 3.47 Tbps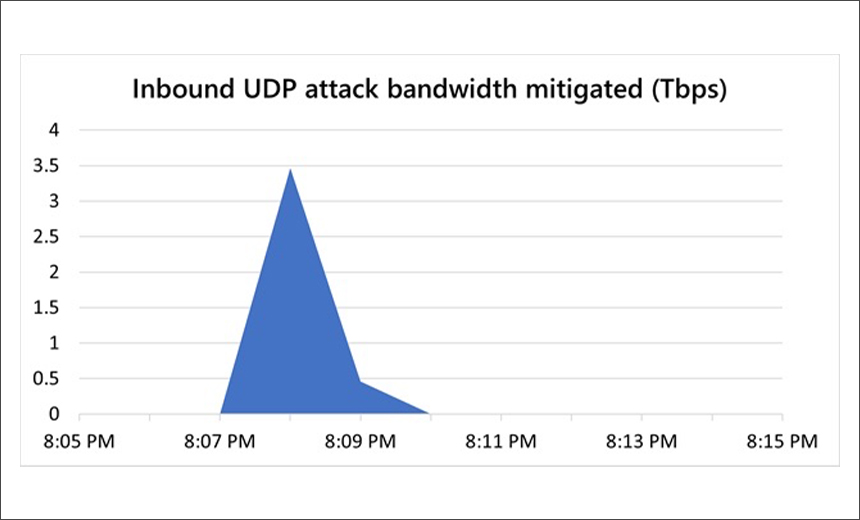
Microsoft successfully mitigated a 3.47 Tbps distributed denial-of-service attack that was targeted at one of its Azure customers from Asia, the company reports in an Azure blog post on DDoS attack trends for Q3 and Q4, published on Tuesday.
See Also: The State of Organizations' Security Posture as of Q1 2018
This is almost 1 Tbps more than the previous largest DDoS attack, reported in October 2021, which had an attack rate of 2.4 terabytes per second at its peak.
Alethea Toh, product manager for Azure Networking, says in the blog post that the company believes this latest attack is "the largest attack ever reported in history."
Attack Details
The post does not mention the exact date or month when the attack took place, but says that it lasted for approximately 15 minutes and originated from approximately 10,000 sources across multiple countries, including the United States, China, South Korea, Russia, Thailand, India, Vietnam, Iran, Indonesia and Taiwan. At its peak throughput of 3.47 Tbps, the DDoS attack attained a packet rate of 340 million packets per second.
Describing the attack vector, Microsoft confirms that it was a user datagram protocol - or UDP - reflection on port 80 using Simple Service Discovery Protocol, Connection-less Lightweight Directory Access Protocol, Domain Name System, and Network Time Protocol . DDoS attacks are generally conducted in short-burst and multiple waves, but this attack consisted of only a single peak, Microsoft says.
December's DDoS Waves
There has been a DDoS tide hitting the Asian Azure customers of Microsoft: "In December, we mitigated two more attacks that surpassed 2.5 Tbps, both of which were again in Asia," the company says.
The first of the two December DDoS attacks was a 3.25 Tbps UDP attack on ports 80 and 443, Microsoft says. The attack spanned just over 15 minutes, as was the case in the earlier attack. But it had four main peaks - the first at 3.25 Tbps, the second at 2.54 Tbps, the third at 0.59 Tbps and the fourth at 1.25 Tbps.
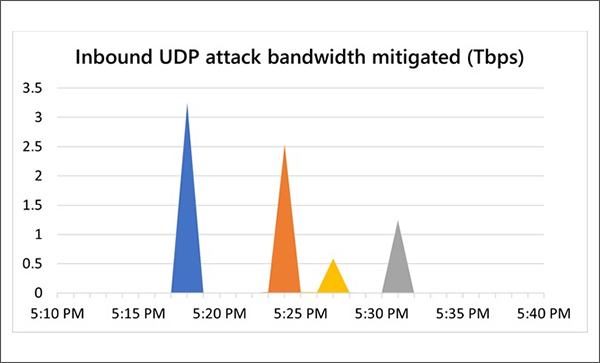
The second notable attack during December was a single-peak 2.55 Tbps UDP flood attack on port 443. "The overall attack lasted just a bit over five minutes," Microsoft says.
In all the above instances, Microsoft says its Azure DDoS Protection platform detected and mitigated even the highest-volume DDoS attacks. To do so, Microsoft says, "Traffic is scrubbed at the Azure network edge before it can impact the availability of services. If we identify that the attack volume is significant, we leverage the global scale of Azure to defend the attack from where it is originating."
Other Findings
Most Attacked Month
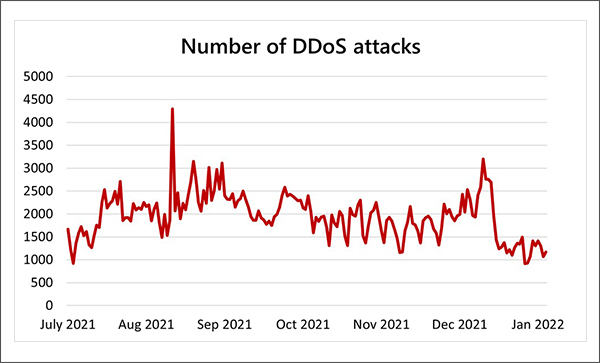
According to the blog post, Azure's Q3 and Q4 report found that its protection platform recorded the highest number of DDoS attacks in August 2021. The single-day record for maximum number of attacks - recorded on Aug. 10 - was 4,296. This is more than double the average number of attacks per day in the first half of 2021.
Shorter Bursts and Longer Attacks
Microsoft says it saw both short-burst and multivector attacks, "although more attacks are lasting longer." Toh says in the post, "We saw a rise in attacks that lasted longer than an hour, with the composition more than doubling from 13% to 27%." She says these longer attacks are typically multiple short-burst attacks that are each ramped up within seconds in terabit volumes.
UDP Spoof Flood Tops the Chart
The blog post says that multivector attacks have remained prevalent in the second half of 2021, although UDP spoof flood-type DDoS attacks remain the top vector, accounting for 55% of all DDoS attacks recorded in the analysis period. This is distantly followed by the TCP ACK flood attack vector at 19%, the post says.
New Attack Vector Emerges
Microsoft's Azure protection service observed new TCP PUSH-ACK flood attacks between October and December's holiday season. This new attack vector was mainly used against Hong Kong, South Korea, and Japan, Microsoft says. "We observed a new TCP option manipulation technique used by attackers to dump large payloads, whereby in this attack variation, the TCP option length is longer than the option header itself."
Microsoft confirms that Azure automatically detected and mitigated this attack with no impact on its customers and did not require any user intervention.
India and East Asia Are Hot Targets
The U.S. receives the most DDoS attacks, accounting for 54%, and relative to other regions, DDoS activity in Europe has halved compared to the first half of 2021. But India has seen a sharp rise and is in second place with 23% of all attacks in the second half of 2021. Microsoft attributes this to the country's digital transformation initiatives, such as the Digital India campaign.
Microsoft says it also has seen a rise in DDoS attacks aimed at East Asian countries, such as Hong Kong, China, Japan and South Korea, and attributed the rise to the expanding gaming footprint in the region. Gaming, it says, is the hardest-hit industry.
Fear Severity, Not Volume
"Today, multi-terabit attacks are not necessarily more effective or dangerous than several 100 Gbps attacks," says Pascal Geenens, director of threat intelligence at Radware. "While still exceptional, there were several terabit-level attacks reported during the last quarter of 2021, and a majority of those were effectively mitigated," he tells Information Security Media Group, citing the Microsoft report.
This is bound to happen as businesses migrate critical resources and applications to the public cloud, Geenens says. "Attackers will have to adapt their tactics and techniques to match the scale of the public cloud providers. Enterprises should not be alarmed by the huge sizes of these attacks, but they need to be aware that DDoS attacks are part of the threat landscape and their severity needs to be measured instead of volume."
To explain why severity matters more than volume, Geenens cites the DDoS attack that took place last weekend during a gaming tournament. "During the Twitch Rivals Squid Games event hosted in Andorra, a DDoS attack no larger than 100 Gbps interrupted the connectivity of the entire country for hours on end. The attack was performed by an individual or group targeting the event by leveraging a paid subscription to a DDoS-for-Hire service. This shows how a small-volume attack can take down an entire country," he says.
Peter Draper, technical director for EMEA at Gurucul, tells ISMG that the reasons attackers use DDoS are many and range from wanting to take services offline to cause havoc to wanting to perform an act of protest or hacktivism.
"One of the concerns around DDoS is what it could be hiding," Draper says. "Oftentimes, DDoS is used to hide other attack vectors that may go unnoticed in the huge volumes of traffic and while IT teams are struggling to deal with the attack."