Malware Takedown Leads to 90 Arrests
Two-Day, Multinational Operation Targeted BlackShades Users
More than 90 individuals have been arrested for their alleged involvement in the creation, distribution and use of the BlackShades malware. The two-day roundup operation, which took place in 16 countries, was a coordinated effort involving international law enforcement agencies, including the U.S. Federal Bureau of Investigation and Europol.
See Also: Revealing the Dark Web: How to Leverage Technologies to Alert and Block Dark Web Access
The European operation was coordinated by Eurojust, a European Union agency that deals with investigations and prosecutions, and supported by the European Cybercrime Centre at Europol, the European Union's law enforcement agency.
During the two-day operation, 359 house searches were carried out worldwide that resulted in the arrest of more than 90 people. More than 1,100 data storage devices suspected of being used in illegal activities were seized, including computers, laptops, mobile telephones, routers, external hard drives and USB memory sticks, Europol says in a May 19 statement. Substantial quantities of cash, illegal firearms and drugs were also seized.
"This case is yet another example of the critical need for coordinated law enforcement operations against the growing number of cybercriminals operating on an EU and global level," says Troels Oerting, head of the European Cybercrime Centre at Europol. "EC3 will continue - together with Eurojust and other partners - to work tirelessly to support our partners in the fight against fraudsters and other cybercriminals who take advantage of the Internet to commit crime."
BlackShades Malware
The BlackShades malware has been sold to thousands of individuals throughout the world, Europol says.
One of the versions of the malware, BlackShades RAT (remote access Trojan), enabled users to remotely and covertly gain complete control over a victim's computer, according to Europol. Once installed on a victim's computer, a user of the RAT can access and view documents, photographs and other files, record all of the keystrokes entered and even activate the webcam on the victim's computer, all of which is done without the victim's knowledge, Europol says.
BlackShades could also be used to carry out large-scaled distributed-denial-of-service attacks, according to Europol.
In a recent case in the Netherlands, an 18-year-old used the BlackShades malware to infect at least 2,000 computers, Europol says.
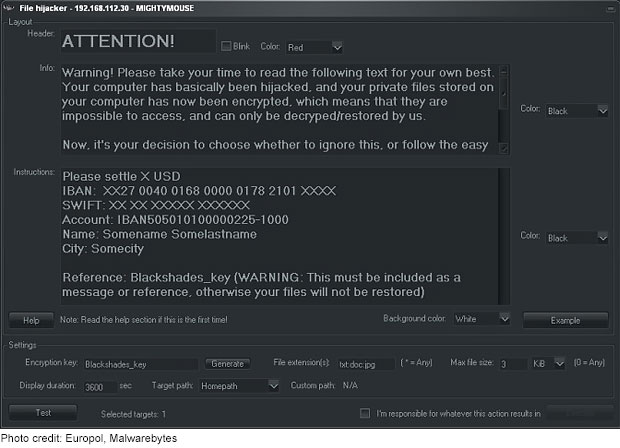
The malware also has the ability to encrypt and deny access to files. Users of the BlackShades malware are provided sample letters they can send along to victims to be used in extortion attempts.
FBI Investigation
The FBI on May 19 announced several charges related to the BlackShades malware bust.
One of the defendants named in the charges, Alex Yucel, allegedly headed the organization that developed and sold the BlackShades remote access tool, according to Leo Taddeo, special agent in charge of the cyber and special operations division for the FBI's New York office.
"Yucel co-created this tool to give customers a method to obtain unrestricted access to another computer without the owner knowing it," Taddeo says. "It required no sophisticated hacking experience or expensive equipment."
Yucel allegedly employed several administrators to facilitate the operation of the organization, including a director of marketing, a website developer, a customer service manager and a team of customer service representatives, Taddeo says. "As a result of their efforts, the BlackShades RAT was purchased by thousands of people in more than 100 countries," he says. "Hundreds of thousands of computers are believed to have been infected."
Over the past week, the FBI conducted interviews of individuals across the U.S. who purchased BlackShades and may have used it to commit cybercrimes, according to Taddeo.
"We also passed leads to foreign law enforcement agencies around the world," he says. "The combined efforts of the FBI and foreign law enforcement marks the BlackShades takedown as one of the largest global cyber operations in history."
In addition to Yucel, the U.S. Attorney's Office for the Southern District of New York announced charges against four other individuals.
Malware Takedown
In addition to the U.S., countries that participated in the BlackShades malware operation include the Netherlands, Belgium, France, Germany, UK, Finland, Austria, Estonia, Denmark, Canada, Chile, Croatia, Italy, Moldova and Switzerland.
Three coordinated meetings were held at Eurojust prior to the two-day operation, Europol says. An operations center was set up at Eurojust during the operation. Representatives of Eurojust, EC3 and the FBI were present at the center, Europol says.
"This case is a strong reminder that no one is safe while using the Internet, and should serve as a warning and deterrent to those involved in the manufacture and use of this software," says Koen Hermans, an assistant at Eurojust. "The number of countries involved in this operation has shown the inherent value in Eurojust's coordination meetings and coordination centers."
















