Business Continuity Management / Disaster Recovery , Fraud Management & Cybercrime , Governance & Risk Management
Crypto-Lock and Tell: Ransomware Gangs Double Down on Leaks
Dedicated Leak Sites Are Likely Driving More Victims to Pay, Security Experts Warn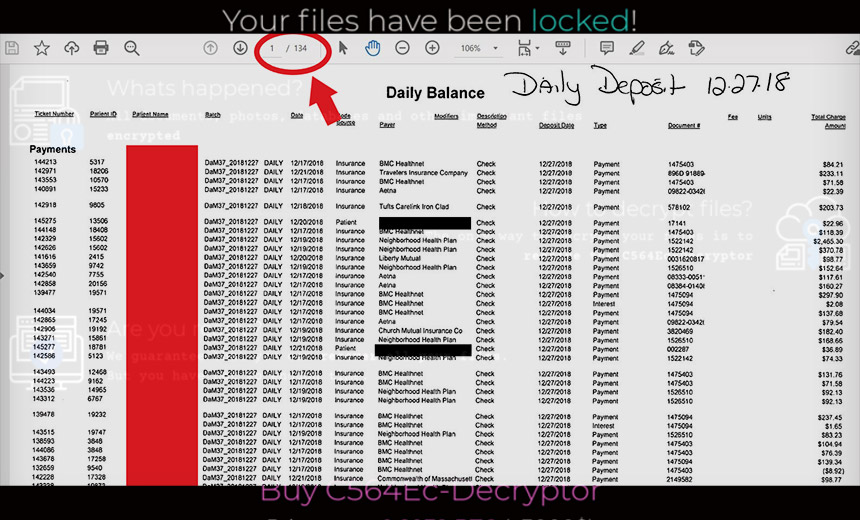
Ransomware continues to pummel organizations, as many attackers don't just bring crypto-locking malware to bear, but also steal and threaten to leak data.
See Also: The State of Organizations' Security Posture as of Q1 2018
While there's no clear data yet about whether these threats do lead more victims to pay, or to pay higher ransoms, a growing number of security experts believe the strategy is proving successful.
Attackers wielding nearly a dozen types of ransomware have been threatening to name and shame victims, followed by trickling out stolen data to try and force victims to pay a ransom demand. Many are now using dedicated leak sites to make their threats as public as possible (see: More Ransomware Gangs Join Data-Leaking Cult.)
In some cases, if victims' bitcoins are not forthcoming, attackers simply dump everything they've stolen from the victim, hoping to make them an example to future targets they hit.
Ransomware Plus Leak Equals Data Breach
Cybercrime is a business, and ransomware currently seems to be the gift that keeps on giving to attackers.
"Organizations that could recover from these [ransomware] attacks without resorting to a ransom payment could avoid the stigma of public disclosure. Attackers recognized this and started exfiltrating data as a component of their attack in an effort to publicly shame those companies into paying,” Clyde Hewitt, executive adviser at cybersecurity consultancy CynergisTek, tells Information Security Media Group. “This tactic largely worked - it is difficult to refute that [data] was accessed inappropriately when it appears on the dark web."
In other words, the ransomware game continues to evolve as attackers seek more ways to boost the return on their investment.
"They are changing tactics and they are innovating, and they are finding new ways to extort payment," says Raj Samani, chief scientist at security firm McAfee. "It was November 2019 that we saw the first examples of leak sites, and that's been copied and replicated because it's successful, and the fact that more people are paying more ransoms means that this is not going to go away. We will see them choke the life out of organizations to extort more and more money. That's fundamentally the trend we're seeing."
From Maze to Beyond
The Maze ransomware gang last year first blazed the data-leaking trail last November, quickly followed by other groups, including DoppelPaymer, MegaCortex, Nemty, Snatch and Sodinokibi, aka REvil, Samani says (see: More Ransomware Gangs Join Data-Leaking Cult).
Other strains of ransomware being used by attackers who also run leak sites include Clop, Sekhmet, Nephilim, Mespinoza, Netwalker and RagnarLocker. Most operate leak sites hosted - as with their bitcoin-payment portals for decryptors - on Tor, which makes them tough for others to take down or trace back to the operators. Such sites can only be reached by the anonymizing Tor browser, although the browser is easy to download.
In recent weeks, victims of data-leaking ransomware gangs have included Australian shipping giant Toll Group, which suffered its second ransomware hit in less than six months, this time by attackers wielding Nefilim, who also stole as-yet-undetermined corporate data.
This week, Scottsdale, Arizona-based managed care company Magellan Health, disclosed that it was hit last month by ransomware via a phishing message designed to impersonate one of its clients, which resulted in attackers stealing information about employees. Exfiltrated records included names, addresses, employee ID numbers, and W-2 or 1099 details, such as Social Security numbers or Taxpayer ID numbers, Magellan says. Some employees' usernames and passwords also got stolen.
Late last month, the Clop gang leaked files it had stolen from King of Prussia, Pennsylvania-based ExecuPharm, which provides clinical research support services to the pharmaceutical industry, after the firm failed to pay a ransom, Bleeping Computer reported.
"Like legitimate businesses, criminal enterprises adopt strategies that have been proven to work," says Brett Callow, a threat analyst at security firm Emsisoft. "The fact that so many groups have followed Maze’s lead and started to exfiltrate data would appear to indicate the strategy works."
Ako: Extra Charge to Delete Data
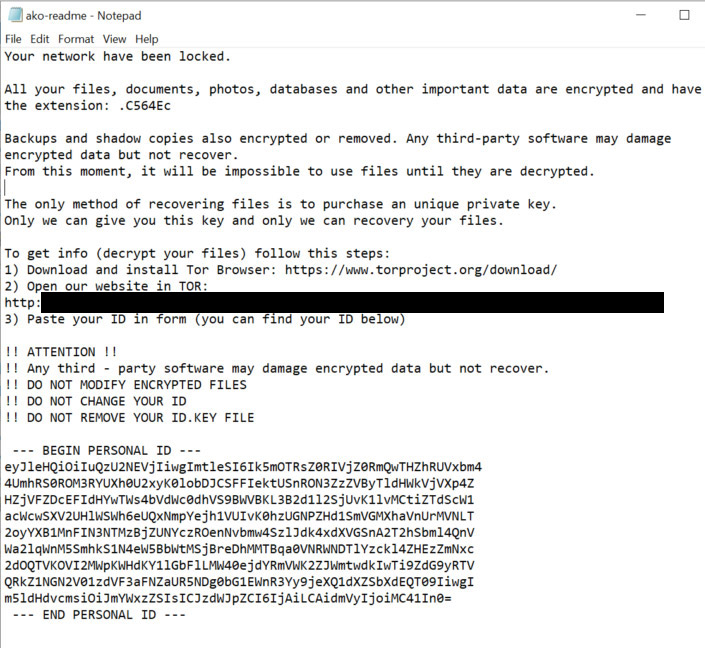
To the list of data-dumping ransomware gangs now add Ako, which says it's now hitting some large victims with two ransoms: One in return for receiving a decryptor, and another to not dump stolen files.
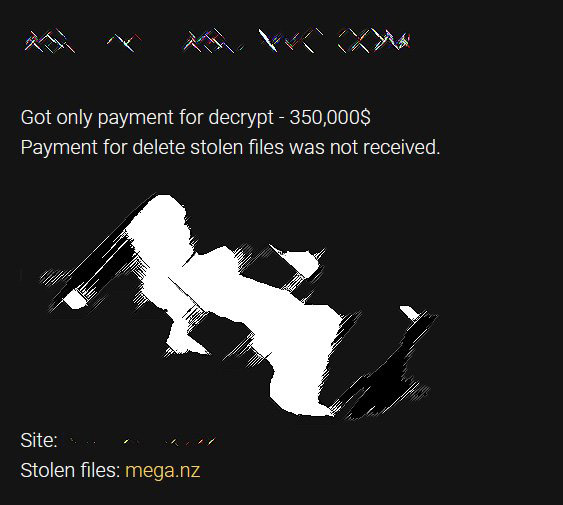
One of the operators behind Ako told Bleeping Computer that the second ransom demand ranges from $100,000 to $2 million, above and beyond however the first ransom demand has been priced.
Based on Ako's dedicated leak site, its recent victims include seven organizations in the medical sector, four businesses and one school district, reports the privacy blogger known as Dissent in a blog post to her Databreaches.net site.
One listed victim, she says, is Massachusetts-based North Shore Pain Management, for which Ako dumped more than 4 GB of employee and patient information, including names, addresses, Social Security numbers, billing information and more.
North Shore Pain Management didn't immediately respond to a request for comment.
Extortion Business is Booming
Unfortunately, many ransomware victims are continuing to pay attackers, despite security experts and law enforcement agencies urging them not to do so.
A survey by Sophos of 5,000 IT professionals found that in 2019, half of their organizations experienced at least one "significant" ransomware attack, leading to 27% paying a ransom, after which most - but not all - received a decryptor that allowed them to restore at least some of the crypto-locked data (see: Ransomware Reminder: Paying Ransoms Doesn't Pay).
The other 73% are ideally able to wipe infected systems and restore from backups or use free decryptors, when available, via such sites as the No More Ransom project. Otherwise, victims that do not pay the ransom may have to kiss the lost data goodbye, hoping that at some point, someone will create a free decryptor for their particular strain. That's one reason the FBI and others urge organizations to always maintain up-to-date, offline backups, while at the same time noting that the choice of whether or not to pay remains up to victims.
When victims do pay, on average, they are paying more. Ransomware incident response firm Coveware, based on more than 1,000 cases it worked in the first quarter of this year, reports that compared to the prior quarter, the average ransom paid by victims to attackers increased by one-third (see: Ransomware: Average Business Payout Surges to $111,605).
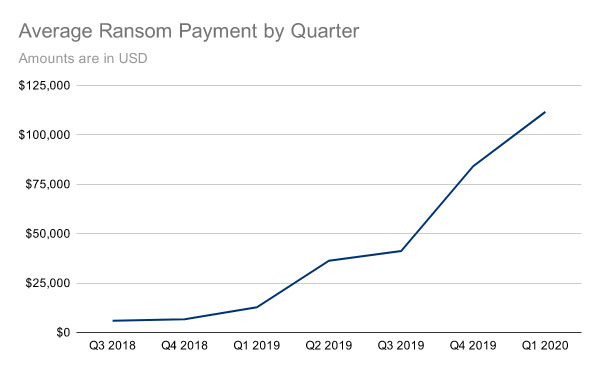
Coveware has also tracked changes in how some gangs are also stealing data. Notably, it says Maze has recently been targeting smaller organizations, from which it is less likely to steal data.
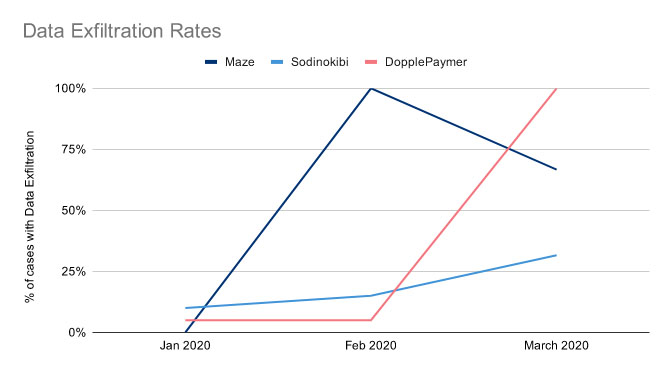
Overall, in the first three months of this year, Coveware says nearly 9% of all cases it worked on also involved attackers stealing data from an organization and threatening to release it publicly, typically via dedicated leak sites, unless victims paid the ransom demand.
"The reason that they're creating leak sites is because the message got across, right? People, I believe, were paying less and less," McAfee's Samani says.
With this extortion tactic apparently continuing to work for more ransomware-wielding gangs, that number of ransomware attacks backed by the threat of data leaks seems set to rise.






















