Fraud Management & Cybercrime , Ransomware
BlackMatter Claims to Shut Ops; Experts Suspect Rebranding
Criminal Group Announced News on Russian Site, Researchers Report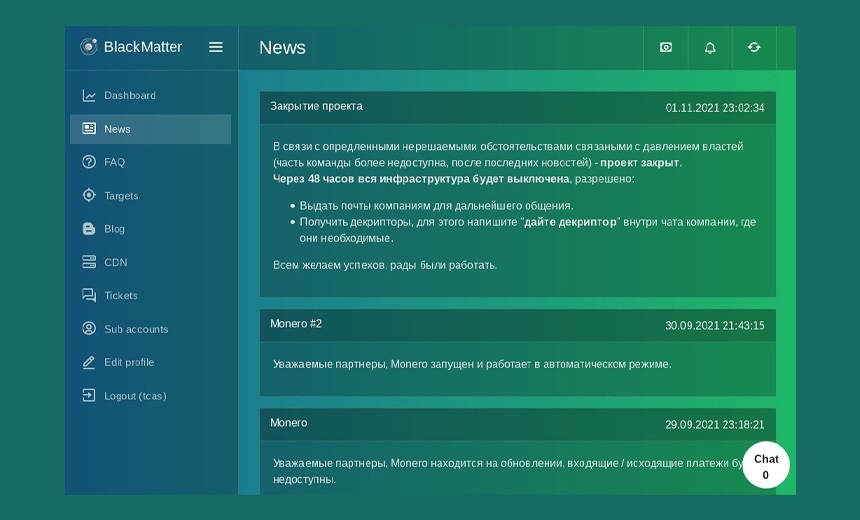
Ransomware-as-a-service provider BlackMatter has ceased operations due to pressure from local authorities, malware research organization vx-underground says, citing an announcement made by the gang on a Russian underground site.
See Also: The Evolution of Phishing and Insights on how to Stay Ahead of Threats
BlackMatter, which is linked with the Coreid cybercrime group, is believed to be a reincarnation of the defunct DarkSide ransomware gang (see: BlackMatter Ransomware Appears to Be Spawn of DarkSide). DarkSide targeted Colonial Pipeline Co. in May and disrupted fuel deliveries along the U.S. East Coast.
"Due to certain unsolvable circumstances associated with pressure from the authorities (part of the team is no longer available, after the latest news) - project is closed," vx-underground says, citing the criminal group's announcement, translated from Russian. "After 48 hours, the entire infrastructure will be turned off, allowing: issue mail to companies for further communication and get decryptor. For this write "give a decryptor" inside the company chat, where necessary. We wish you all success, we were glad to work."
Vx-underground did not immediately respond to Information Security Media Group's request for additional details about the announcement.
Rebranding Operation, Some Experts Say
Some experts believe that the group may only be rebranding.
According to Carl Wearn, head of e-crime at IT security company Mimecast, it is highly unlikely to be the end of the threat actors behind BlackMatter. "This looks like a classic rebrand or splintering," he says.
"Cybercriminals that are making this much money rarely give up, as the greed that drives them to commit the crimes in the first place rarely allows them to stop. Many criminal organizations claim to shut down in an attempt to reduce the heat, just to splinter, or return after a brief hiatus under a different name," Wearn tells ISMG.
According to Jake Williams, a former National Security Agency elite hacking team member and currently the CTO of cybersecurity firm BreachQuest, ransomware operators are feeling the pressure of decreased payment rates, owing largely to better backups and other preparation by victims.
"This preparation has made the use of double extortion methods necessary to regain some leverage and compel payment. Of course even after payment, there's little incentive for the operators to delete data. With groups rebranding so often, the reputation damage from leaking data after a group 'shuts down' would be minimal," Williams notes.
Any successful criminal group - such as BlackMatter - has considerable funds and resources that will enable them to reinvent themselves, says Steve Forbes, government cybersecurity expert at cybersecurity company Nominet.
"If criminals feel that a part of their operation is compromised or that law enforcement is closing in, they will naturally want to distance themselves from their existing activities and infrastructure as quickly as possible. But given the lucrative activity of RaaS, we are likely to see them reappear in the near future," he says.
"This could, of course, be a deliberate ploy if they feel that their communications with affiliates are being monitored, perhaps to divert the attention of law enforcement to other ransomware gangs," Forbes adds.
Custom Data Exfiltration Tools
Separately, days before the news of the disbandment surfaced, a team of threat hunters at cybersecurity company Symantec found that an affiliate of the BlackMatter ransomware group uses a custom data exfiltration tool for its attacks.
"Exmatter, which was discovered by Symantec’s threat hunter team, is designed to steal specific file types from a number of selected directories and upload them to an attacker-controlled server prior to deployment of the ransomware itself on the victim’s network," the researchers at Symantec note.
Symantec researchers say that Exmatter is the third such custom data exfiltration tool developed by ransomware operators, following the discovery of the Ryuk Stealer tool and StealBit, which is linked to the LockBit ransomware operation.
Williams notes that the creation of data exfiltration tools shows that criminal groups are not only worried about standardizing their encryption operations, but also extortion operations. "The mere existence of the tool shows how important the double extortion process has become for operators," he says.
Tying the two bits of news together, Peter Mackenzie, director of incident response at Sophos, says that the ransomware attack against Colonial Pipeline resulted in the shutting down of DarkSide ransomware, which shortly returned under the name of BlackMatter.
"While the name was different, the core ransomware code was not, and it had the same weaknesses that allowed free decryptors to be produced. In October, a security company announced they had a decryptor for BlackMatter and had been secretly helping victims. Taking these factors into account, it is likely this is yet another ransomware group pretending to shut down, when in reality, it is just a rebrand and launch of a new improved version sometime soon in the future,” he says.
Crackdown Caused Shutdown?
BlackMatter's shutdown announcement follows the arrest of 12 individuals by Europol for their suspected roles in ransomware attacks against critical infrastructure across the world.
These actors are believed to have affected more than 1,800 victims in 71 countries and are known to have targeted large corporations, causing business disruption, according to Europol.